Wi-Fi Woes? MetaGeek App’s Wi-Fi 7 Upgrade...
Bryan Lee
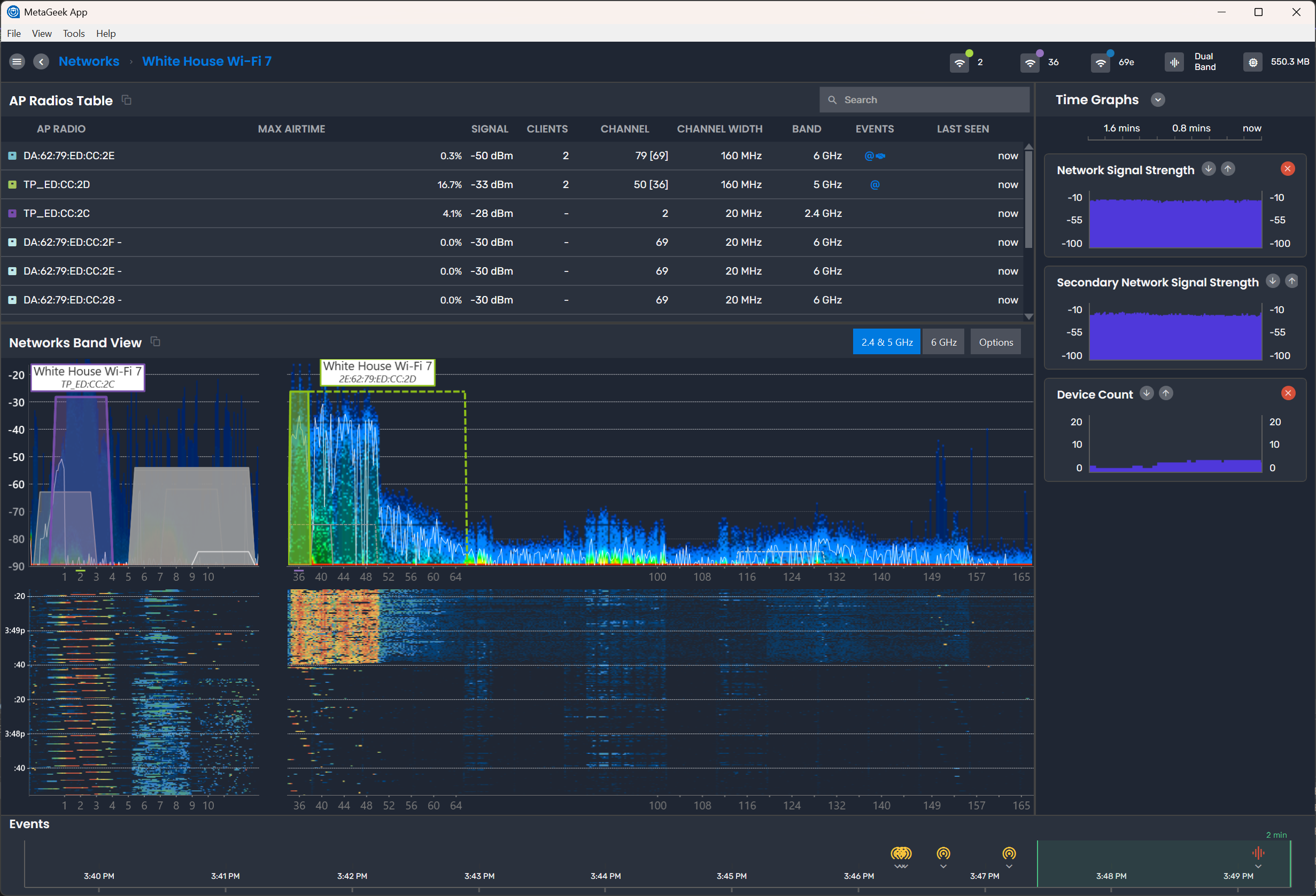
The MetaGeek App supports 802.11be packet capture on 2.4, 5 and 6 GHz
As the Internet of Things (IoT) has gained popularity and momentum with Wi-Fi Crockpots and “smart” toothbrushes, it was only a matter of time until IoT devices were hacked…
As the Internet of Things (IoT) has gained popularity and momentum with Wi-Fi Crockpots and “smart” toothbrushes, it was only a matter of time until IoT devices were hacked… and that time has come. The recent DDoS attacks haven’t relied on hacked consumer devices though, they have been hijacking early industrial CCTV webcams and other enterprise equipment. Which means network administrators have the potential to prevent similar attacks from happening.

Six weeks ago the first major attack using IoT devices occurred when the Mirai botnet attacked Krebsonsecurity.com. At approximately 620 Gbps of traffic this attack was double the size of the largest attack Akamai had previously seen.
After the massive attack on krebsonsecurity.com the source code for Mirai was released into the wild, allowing less skilled hackers to take advantage of it. Less than two weeks later another major attack occurred, this time against Dyn DNS, which impacted thousands of sites, including PayPal, Twitter, Reddit, Github, Amazon, Netflix, and Spotify. This attack was likely not financially or politically motivated as there has been no indications of extortion against Dyn or any of the sites affected by the attack. Another attack in early November used a Mirai botnet to attack a mobile telecom provider in Liberia. This attack sustained about 500 Gbps of traffic.
With the Mirai source code now publicly available the frequency and intensity of these botnet attacks is likely to increase.
Mirai malware primarily targets circa 2004 DVRs and CCTV cameras, not consumer devices. Most of the compromised devices can be traced back to a single manufacturer: Xiongmai Technologies, who has since recalled 4.3 million camera products from the U.S. market, but these devices are all white labeled and sold under other brands, so it is difficult for end-users to know if they own any of the recalled devices.

An IP camera module from Hangzhou Xiongmai Technology. Credit: Xiongmai
Many of these devices use UPnP to open Telnet and SSH ports along with an HTTP port, with the Telnet and SSH passwords being hardcoded in the device firmware. Mirai contains a list of about 60 common username/password combinations (like root/12345) to gain access to the IoT device. It is also trivially easy to bypass the web authentication present on all XiongMai Technologies devices running “NetSurvaillance” software (“uc-httpd”).
Once a device is infected with Mirai it continues to perform its original function while also searching for other devices to infect and checks for commands from the command and control (C&C) server. Mirai is not persistent, so the devices can be wiped clean with a power cycle, but unless prevention measures are taken the device will likely be reinfected.
ISPs are beginning to take measures to block traffic associated with Mirai and other botnet attacks. But the continued flood of “connected devices” like The Hello Barbie Dreamhouse and Kittyo (“Play with your cat. Even when you’re not home”) present new targets for hackers… keeping all of us in the Wi-Fi network management business employed… and stressed.
Subscribe to Signifi Personal.

If you're ready to take control of your Wi-Fi and make it feel like magic for your users, we are here to help.